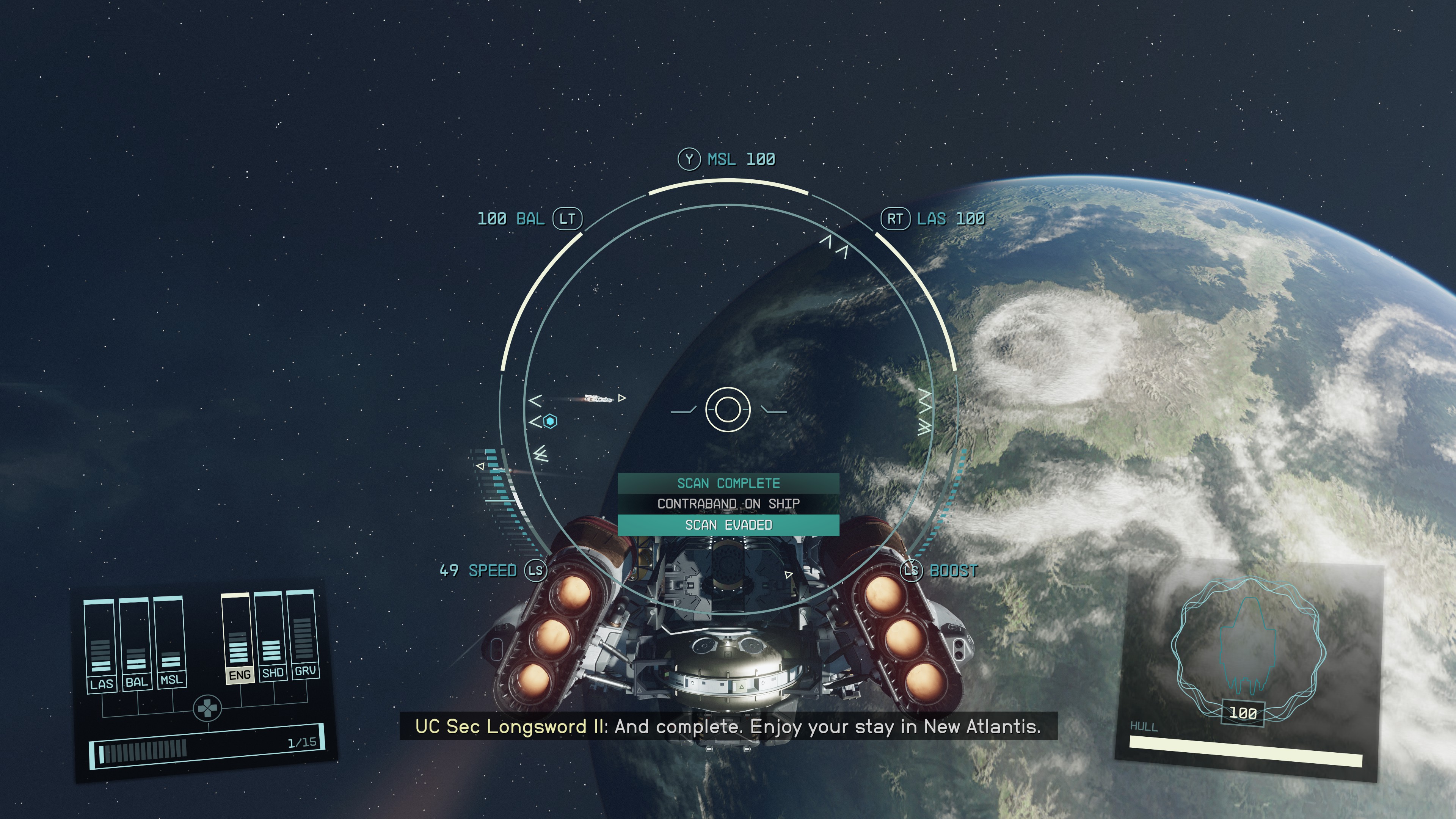
In the vast expanse of the Settled Systems, the movement of high-value, restricted cargo—commonly referred to as contraband—is less a matter of luck and more a rigorous application of advanced flight technology. For pilots operating on the fringes of United Colonies or Freestar Collective space, the challenge is not merely the distance traveled, but the sophisticated sensor arrays that guard the orbital perimeters of major settlements. To successfully transport and offload these goods, one must possess a deep understanding of sensor evasion, shielded cargo stabilization, and stealth-oriented navigation protocols.

Managing contraband requires more than a fast engine; it necessitates a sophisticated suite of electronic countermeasures and structural modifications. This guide examines the technical specifications of flight systems required to bypass high-frequency orbital scans and the stabilization technologies used to keep illicit signatures neutralized during transit.
The Physics of Detection: Understanding Sensor Arrays and Scanners
Before a pilot can hope to bypass a security perimeter, they must first understand the mechanics of the technology used to detect them. Orbital scanners utilized by planetary security forces are not simple visual cameras; they are complex multi-spectral arrays designed to detect atomic signatures, heat blooming, and electromagnetic anomalies within a ship’s hull.
Electromagnetic Interference and Signature Management
Every piece of cargo, particularly high-density illicit materials like harvested organs or xenowarfare tech, emits a distinct electromagnetic (EM) signature. Standard cargo holds are designed for structural integrity rather than signal masking. When a security drone or orbital station sweeps a vessel, it pulses the ship with a wide-band frequency. If the return signal indicates a density or radiation profile that doesn’t match the ship’s manifest, the “contraband detected” alert is triggered.
Advanced flight technology focuses on “Signature Management,” which involves the use of internal dampeners. These dampeners are integrated into the ship’s power grid to create a localized EM vacuum, effectively pulling the stray emissions of the cargo into the ship’s own power cycle, masking the presence of unauthorized materials.
The Role of Multi-Spectral Scanning in Orbital Security
Security forces use a combination of LIDAR, RADAR, and passive thermal imaging to build a 3D composite of any ship entering their airspace. To counter this, pilots must utilize “Profile Reduction” flight modes. This technology adjusts the ship’s exterior profile and minimizes the cross-section available for scanning. By tilting the vessel at a specific angle relative to the scanning source—a maneuver controlled by automated stabilization software—the pilot can reflect the majority of the scanning pulses away from the receiver, much like stealth aircraft technology used in atmospheric flight.
Shielded Cargo Technology: Stabilization and Signal Dampening
The most critical piece of flight hardware for any smuggler is the shielded cargo hold. Unlike standard containers, these units are marvels of aerospace engineering, designed to isolate their contents from the external environment while maintaining a perfectly neutral electronic profile.
Constructing Isolated Compartments for Electronic Neutrality
Shielded cargo holds are lined with layers of lead, mercury-doped polymers, and superconducting meshes. This construction serves a dual purpose: it prevents external scanners from penetrating the hold and prevents internal signals from leaking out. However, the weight and density of these materials can disrupt a ship’s center of mass.
Modern flight stabilization systems must be recalibrated when installing shielded holds. The software must account for the “dead weight” of the shielding, which does not react to inertial dampeners in the same way as standard hull plating. A failure in stabilization during a high-G turn could result in the cargo shifting, creating a kinetic signature that orbital sensors can easily detect as an anomaly.
Integration of Active Frequency Scramblers
While passive shielding is effective, it is rarely enough to guarantee passage through high-security zones like New Atlantis or Akila City. This is where active frequency scramblers come into play. These devices are integrated directly into the ship’s communication and navigation arrays.
When the scrambler detects an incoming scan pulse, it calculates the frequency in milliseconds and emits an “anti-signal” that phase-cancels the scan. This technology requires immense processing power and precise synchronization with the ship’s flight computer. If the scrambler is out of sync with the ship’s movement, the resulting “ghosting” effect on the scanner’s screen will immediately alert security to the presence of stealth technology.

Navigation Protocols for Low-Profile Transit
What you do with contraband is just as important as how you hide it. The flight path chosen is a technological component of evasion. Moving from point A to point B in a straight line is the easiest way to get caught. Professional pilots utilize “Dynamic Pathing” to stay beneath the “noise floor” of planetary sensors.
Gravity Well Utilization for Signature Masking
One of the most effective navigation techniques involves “Gravity Masking.” By maneuvering a ship close to a moon or a large asteroid, a pilot can use the natural celestial body to block the direct line of sight from orbital sensor platforms.
Advanced navigation computers can plot a “shadow trajectory,” where the ship stays within the gravitational and electromagnetic shadow of a planet’s natural satellite. This requires high-precision stabilization systems to ensure the ship doesn’t drift into the atmosphere or collide with debris, as any sudden burst of the thrusters to correct course would create a thermal flare visible to scanners across the system.
Automated Flight Pathing and Decentralized Hubs
To offload contraband, one must often travel to decentralized hubs like The Key in the Kryx system or independent outposts in the Porrima system. Navigation to these locations often involves “Dark Jumps”—grav-jumps to unmarked coordinates in deep space followed by sub-light approaches.
This process relies heavily on autonomous flight algorithms. Because these trade routes are not monitored by the United Colonies’ navigational beacons, the ship’s local sensors must do all the heavy lifting. The technology involves mapping real-time debris fields and gravitational anomalies without the aid of a localized GPS, requiring a robust sensor suite that operates on a “listen-only” (passive) mode to avoid detection.
Advanced Systems for Evasive Maneuvering
If a scan fails and security forces turn hostile, “what to do with contraband” shifts from evasion to survival. The flight technology required for a clean escape is vastly different from that used for stealth.
Thrust Vectoring and Inertial Dampeners
Escaping a security cordon requires extreme agility. Thrust vectoring—the ability to tilt the engine nozzles independently—allows a ship to rotate and flip on its axis without changing its flight path. This is essential for keeping the strongest part of the ship’s shields facing the attackers while the Grav Drive spools up.
The bottleneck in this scenario is often the pilot’s own body. High-speed maneuvers generate massive G-forces. High-end flight tech includes advanced inertial dampeners that create a localized field of stable gravity within the cockpit. This allows the pilot to perform 180-degree “flip-and-burn” maneuvers at high speeds, which is often necessary to break a target lock and initiate a jump to another system.
The Ethics of Autonomous Stealth Algorithms
As flight technology evolves, the role of Artificial Intelligence in smuggling becomes more prominent. Some advanced systems now feature “Auto-Evasion” modes, where the ship’s computer takes over the controls the moment a scan is detected. These algorithms can make micro-adjustments to the ship’s power output—dimming the lights, cutting non-essential life support, and venting heat in a controlled direction away from the scanners.
However, the use of such autonomous tech remains a point of contention among veteran pilots. While a computer can react faster than a human, it lacks the “intuitiveness” to handle unpredictable environmental variables, such as a sudden solar flare or an unexpected patrol route change. Mastering the interplay between human decision-making and autonomous flight assistance is the hallmark of a truly skilled high-risk cargo transporter.
Conclusion: The Synergy of Tech and Technique
Handling contraband in the Settled Systems is a multifaceted challenge that sits at the intersection of advanced engineering and precision piloting. From the lead-lined walls of shielded cargo holds to the complex mathematics of phase-canceling scramblers, the technology of flight is the only thing standing between a massive payday and a life in a correctional facility.
To succeed, a pilot must treat their vessel not just as a vehicle, but as a sophisticated electronic warfare platform. By mastering sensor signatures, optimizing navigation through gravitational masking, and utilizing the latest in thrust vectoring and stabilization, one can turn the most illicit cargo into a routine delivery. In the end, the “what to do” with contraband is simple: protect it with the best technology available, move it with the quietest systems engineered, and always stay one step ahead of the scan.
