As the world of unmanned aerial vehicles (UAVs) transitions from localized radio-controlled gadgets to sophisticated, cloud-connected IoT devices, the underlying networking infrastructure has become increasingly complex. One of the most critical components in this modern tech stack is the Web Application Firewall, or WAF. While traditionally associated with enterprise websites and e-commerce platforms, the role of WAF in networking has become a cornerstone of “Tech & Innovation” within the drone industry.
In the context of modern flight technology—specifically regarding autonomous flight, remote sensing, and large-scale mapping—a WAF serves as a specialized security layer. It is designed to filter, monitor, and block HTTP/HTTPS traffic to and from a web application or API. For drone operators and developers, this means protecting the vital links between the aircraft, the ground control station (GCS), and the cloud-based servers that process complex flight data.
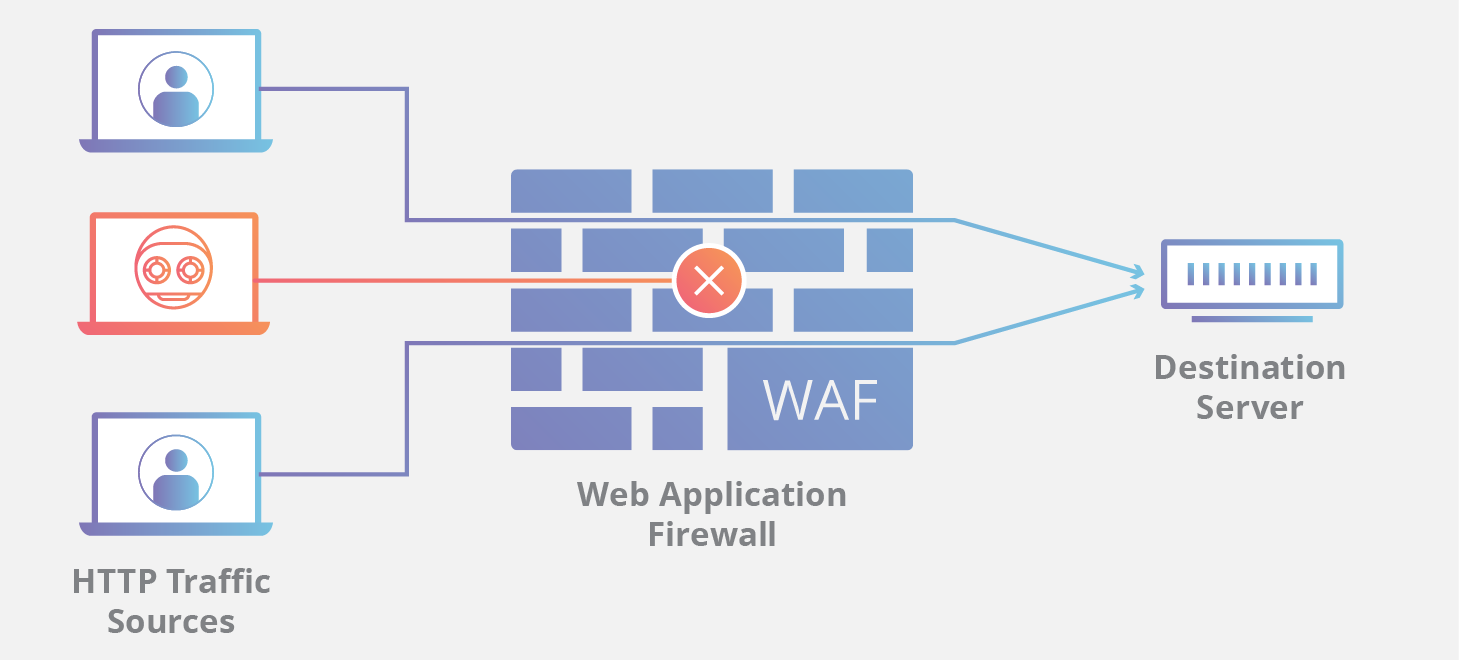
The Architecture of WAF in Modern Drone Ecosystems
In the era of drone-as-a-service and autonomous fleet management, drones are no longer isolated units. They are nodes in a massive network. When a drone performs a mapping mission or a remote sensing operation, it frequently communicates with web-based APIs to upload telemetry, download flight paths, or stream real-time sensor data. This is where the WAF enters the networking equation.
Protecting API Endpoints for Fleet Management
Modern autonomous drones rely on Application Programming Interfaces (APIs) to receive commands from remote operators or automated dispatch systems. These APIs are the “doors” to the drone’s control center. Without a WAF, these doors are vulnerable to malicious actors who might attempt to send unauthorized commands or intercept sensitive data. A WAF acts as a gatekeeper, inspecting every request made to the fleet management server to ensure it conforms to established security protocols. By validating that the traffic is legitimate, the WAF prevents unauthorized users from hijacking drone missions or accessing proprietary flight logs.
Securing Telemetry and Real-Time Data Streams
Remote sensing and mapping generate enormous amounts of data. Whether it’s LiDAR point clouds, multispectral imagery, or standard thermal data, this information is often streamed to the cloud for real-time processing. A WAF in this networking environment ensures that the data stream remains untainted. It protects against “Man-in-the-Middle” (MitM) attacks and ensures that the telemetry data—which includes critical GPS coordinates and altitude information—has not been tampered with during transit. This integrity is vital for autonomous flight, where a slight deviation in data could lead to catastrophic failure.
Key Features of WAF Relevant to Remote Sensing and Mapping
Remote sensing and mapping are some of the most data-intensive applications in the drone industry today. These operations require high-performance networking that can handle large file transfers while maintaining rigorous security standards. The integration of a WAF into these workflows provides specific protections that standard network firewalls simply cannot offer.
Mitigating DDoS Attacks on Flight Servers
For companies operating autonomous fleets, uptime is non-negotiable. A Distributed Denial of Service (DDoS) attack can flood a server with so much junk traffic that it becomes unresponsive, effectively “grounding” the entire fleet by cutting off their connection to the control cloud. A WAF is uniquely equipped to handle this because it can distinguish between legitimate traffic (the drones) and malicious botnet traffic. By filtering out the noise at the application layer, the WAF ensures that the drones remain connected to their mapping software and navigation databases even during a sustained cyber-attack.
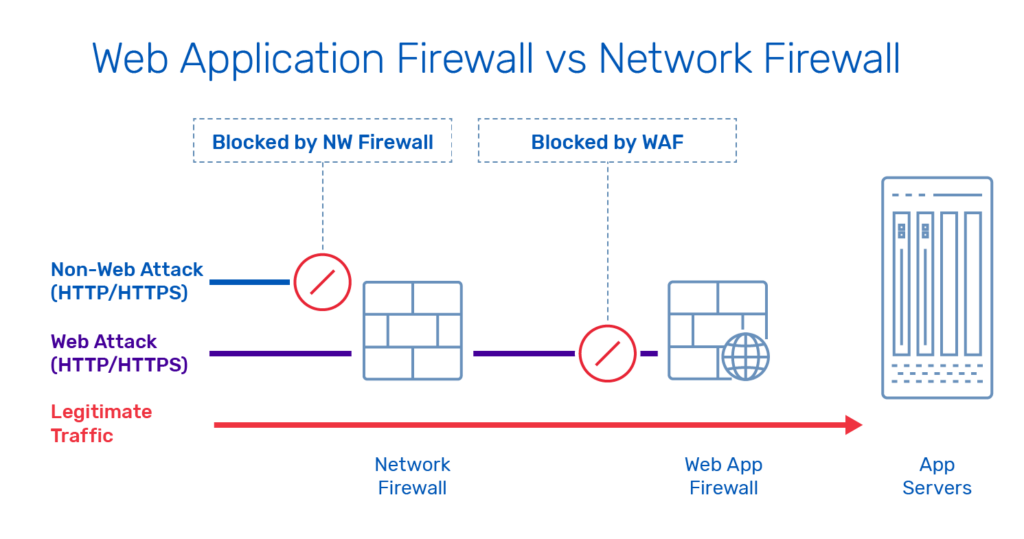
Preventing SQL Injection in Geographic Databases
Mapping drones frequently interact with massive geographic and spatial databases. These databases store everything from prohibited no-fly zones to high-resolution 3D terrain models. A common cyber-attack involves “SQL Injection,” where an attacker sends a malicious query to a database to steal or delete data. A WAF monitors these queries. If it detects a suspicious pattern that looks like an attempt to manipulate the database, it blocks the request instantly. This ensures that the environmental data used for autonomous obstacle avoidance and path planning remains accurate and secure.
Rate Limiting for Autonomous Flight Control
In the context of autonomous flight, the frequency of data transmission is critical. However, an unusually high volume of requests from a single source can indicate a compromised drone or a “brute-force” attempt to crack a control password. WAFs allow for “rate limiting,” which sets a threshold for how many requests a specific IP address can make in a given timeframe. This prevents the networking infrastructure from being overwhelmed and ensures that the bandwidth is prioritized for critical flight maneuvers and real-time sensor feedback.
Integrating WAF with AI and Autonomous Systems
The “Innovation” aspect of the drone industry is currently dominated by Artificial Intelligence (AI). From AI follow modes to autonomous decision-making in complex environments, these systems require a secure “brain” that often resides in the cloud. The networking that supports this AI must be robust, and the WAF is the shield that protects these advanced algorithms.
Behavioral Analysis and Anomaly Detection
Advanced WAFs now incorporate machine learning to move beyond simple rule-based security. In a drone networking environment, the WAF can learn the “normal” behavior of a fleet. For example, it knows that a mapping drone typically uploads 500MB of data every 20 minutes from a specific geographic region. If the WAF suddenly sees a 5GB upload from an unrecognized location, it flags this as an anomaly. This behavioral analysis is crucial for identifying “zero-day” threats—attacks that have never been seen before—protecting the autonomous systems from sophisticated corporate espionage or sabotage.
Zero Trust Security Models in UAV Networks
As we push the boundaries of autonomous flight, the industry is moving toward a “Zero Trust” model. This means that no device, even a drone within the company’s own fleet, is trusted by default. Every single request must be verified. A WAF is the primary tool for implementing Zero Trust at the application level. It forces every drone to authenticate its identity and verify its permissions before it can access sensitive mapping data or receive new flight instructions. This layered approach to networking ensures that even if one drone is physically captured or compromised, the rest of the network remains secure.
The Future of WAF in Drone Networking and Edge Computing
As we look toward the future of tech and innovation in the drone space, the conversation is shifting toward edge computing. To reduce latency for high-speed autonomous racing or real-time obstacle avoidance, data processing is moving closer to the drone, often on localized “edge” servers. This transition is changing the way WAFs are deployed.
Moving WAF to the Edge for Lower Latency
In traditional networking, traffic might travel thousands of miles to a central server to be inspected by a WAF. For a drone traveling at 60 mph, even a few milliseconds of delay (latency) can be the difference between a successful mission and a crash. The next generation of WAF technology is being deployed at the “edge.” By placing the WAF closer to the drone’s physical location—often in 5G towers or local ground stations—security checks can happen in real-time without slowing down the critical data flow required for autonomous flight.
AI-Driven Security for Next-Gen Autonomous Fleets
The future of drone networking will likely see the WAF and the drone’s AI becoming more deeply integrated. Imagine a scenario where a WAF detects a localized jamming attempt or a spoofing attack. Not only would the WAF block the malicious traffic, but it would also instantly communicate with the drone’s autonomous flight controller to trigger a “Return to Home” (RTH) protocol or an emergency landing. This level of synergy between networking security and flight technology represents the pinnacle of innovation in the UAV sector.
In summary, when we ask “what is WAF in networking” within the drone industry, we are talking about the invisible shield that makes the modern drone revolution possible. As drones become more autonomous and more reliant on the cloud for mapping, sensing, and AI-driven flight, the WAF ensures that these innovations remain safe, reliable, and secure from the evolving threats of the digital landscape. Without the sophisticated protection of a Web Application Firewall, the dream of a fully connected, autonomous aerial future would remain grounded by the risks of the open web.
