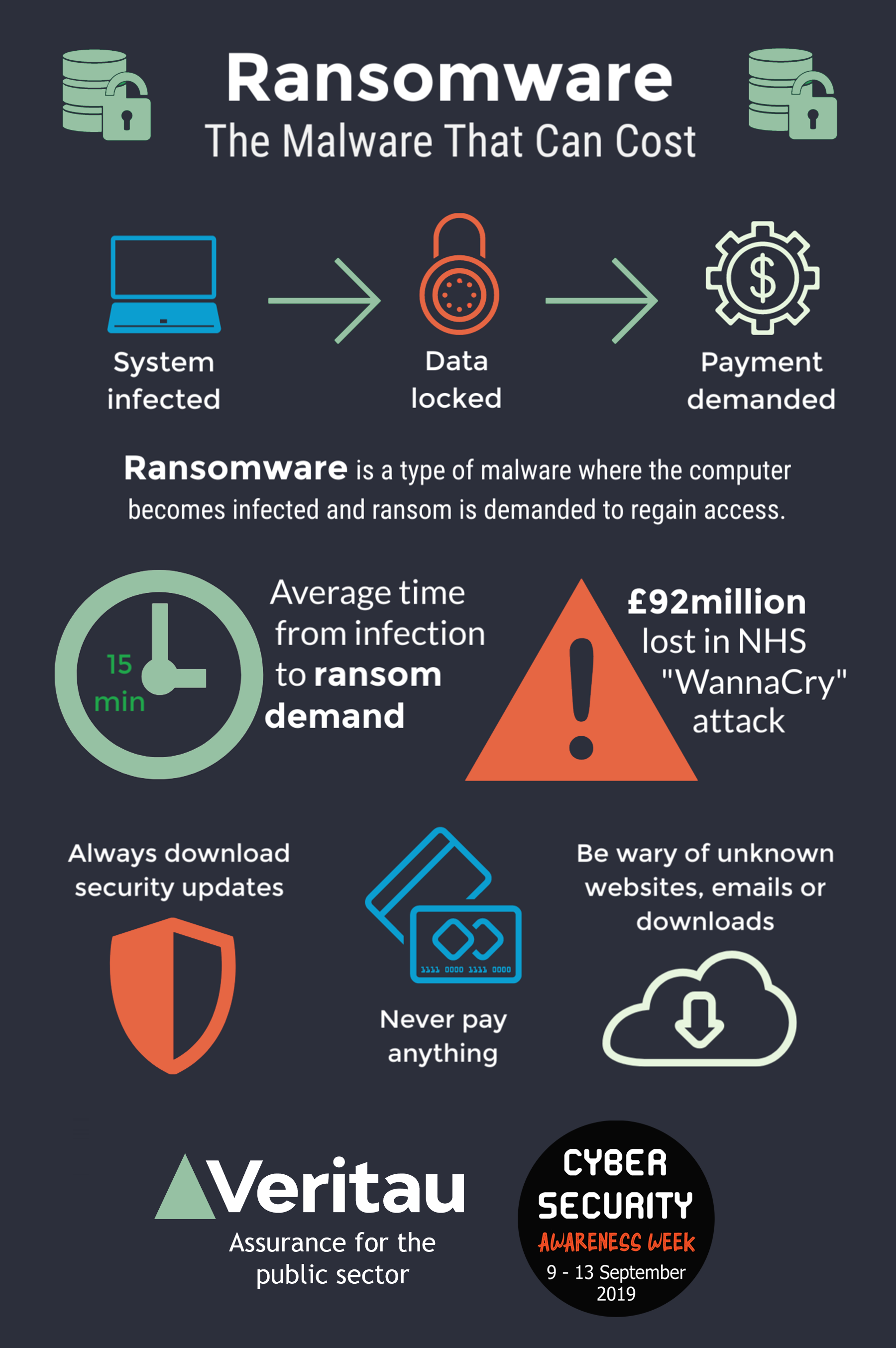
Ransomware is a type of malicious software (malware) that encrypts a victim’s files or locks their entire system, making it inaccessible. The cybercriminal then demands a ransom payment, typically in cryptocurrency, in exchange for the decryption key or the restoration of access. This insidious form of cyberattack has become a pervasive threat to individuals, businesses, and even governments worldwide, crippling operations, causing significant financial losses, and compromising sensitive data. Understanding the nature of ransomware, its various forms, and how it infiltrates systems is the first crucial step in defending against this escalating digital menace.
The Anatomy of a Ransomware Attack
Ransomware attacks are sophisticated and often follow a predictable, albeit highly damaging, pattern. The initial infiltration is usually facilitated through deceptive means, exploiting human error or system vulnerabilities. Once inside, the malware meticulously works to achieve its objective: rendering data or systems unusable, thereby creating leverage for the extortion.
Initial Infiltration Vectors
The pathways through which ransomware gains entry into a system are diverse, often preying on user trust or technical loopholes.
Phishing and Social Engineering
One of the most common entry points for ransomware is through phishing emails. These emails are expertly crafted to appear legitimate, often impersonating well-known organizations, colleagues, or even friends. They typically contain malicious attachments or links. An unsuspecting user clicking on the link might be directed to a fraudulent website that downloads the malware, or opening the attachment, which could be a disguised executable file or a document with embedded malicious macros, could trigger the infection. Social engineering tactics extend beyond email, encompassing deceptive phone calls or instant messages designed to elicit sensitive information or prompt users to download infected files.
Exploiting Software Vulnerabilities
Ransomware can also exploit unpatched security flaws in operating systems, applications, or network devices. Cybercriminals actively scan for systems running outdated software that has known vulnerabilities for which patches have been released but not yet applied. By leveraging these weaknesses, they can gain unauthorized access and deploy the ransomware without any user interaction. This highlights the critical importance of maintaining up-to-date software and applying security patches promptly.
Drive-by Downloads and Malvertising
Another method involves compromised websites or malicious advertisements (malvertising). Users may unknowingly visit a website that has been infected with malicious code. This code can automatically download and install ransomware onto their system without the user even clicking on anything – a process known as a drive-by download. Similarly, malicious ads displayed on legitimate websites can serve as a delivery mechanism, redirecting users to exploit kits or directly downloading malware.
Encryption and Data Lockout
Once the ransomware has successfully infiltrated a system, its primary function is to make data inaccessible. This is achieved through robust encryption algorithms, rendering files and systems unusable without the corresponding decryption key.
Symmetric and Asymmetric Encryption
Ransomware utilizes encryption to lock down victim data. Most modern ransomware employs asymmetric encryption, a two-key system. A public key is used to encrypt the data, and only the corresponding private key can decrypt it. The cybercriminal holds the private key and uses it to demand payment. In some cases, symmetric encryption might be used, where a single key encrypts and decrypts data. Regardless of the method, the result is the same: the victim’s data is rendered illegible and useless.
System Locking and Data Exfiltration
Beyond file encryption, some forms of ransomware can lock the entire operating system, presenting a full-screen ransom demand. In a more aggressive tactic, known as “double extortion,” attackers not only encrypt data but also exfiltrate (steal) sensitive information before encryption. They then threaten to release this stolen data publicly or sell it on the dark web if the ransom is not paid, adding another layer of pressure and deterring victims from simply restoring from backups.
Types of Ransomware
The ransomware landscape is constantly evolving, with attackers developing new variants and employing diverse tactics to maximize their illicit gains. Understanding these different types can help in identifying potential threats and implementing appropriate protective measures.
Crypto-Ransomware and Locker-Ransomware
The two primary categories of ransomware are crypto-ransomware and locker-ransomware, distinguished by their methods of disruption.
Crypto-Ransomware: Encrypting Your Digital Life
Crypto-ransomware is the most prevalent and damaging type. As its name suggests, it encrypts files on the victim’s computer, making them inaccessible. This can include documents, photos, videos, databases, and any other type of digital data. The ransom demand is for the decryption key to restore access to these encrypted files. The encryption strength can vary, but often it’s robust enough to make manual decryption virtually impossible without the key.
Locker-Ransomware: Locking You Out
Locker-ransomware, while less common today than crypto-ransomware, focuses on preventing access to the infected device altogether. It locks the user out of their operating system, displaying a full-screen message demanding payment. While it doesn’t typically encrypt files, the inability to access the system and its data can be just as disruptive, especially for businesses.
File-Specific vs. System-Wide Encryption
The scope of the ransomware’s impact can also vary, affecting specific files or the entire system.
Targeting Critical Files
Some ransomware variants are designed to target specific types of files or files in particular locations, such as user documents or shared network drives. This targeted approach can be devastating for organizations that rely heavily on these specific data sets.
Full System Lockdowns
Other ransomware aims for a complete system lockdown, encrypting everything from the operating system files to user data. This can render a machine completely inoperable and require a full system reformat and data restoration.
Other Emerging Variants
The ingenuity of cybercriminals means new ransomware strains and tactics are continually emerging.
Scareware
Scareware is a type of malware that tricks users into believing their computer is infected with viruses or other malicious software. It then prompts them to pay for fake software to remove these non-existent threats. While not strictly ransomware in the encryption sense, it uses fear and deception to extract money.
Wiper Malware
Wiper malware, while distinct from ransomware, often shares delivery mechanisms. Its primary goal is not to extort money but to permanently destroy data, making recovery impossible. It’s often used in state-sponsored attacks or as a destructive tool rather than for financial gain.
Defending Against the Ransomware Threat
The escalating prevalence and sophistication of ransomware attacks necessitate a multi-layered and proactive approach to cybersecurity. Prevention, detection, and rapid response are all critical components of a robust defense strategy.
Proactive Prevention Strategies
The most effective way to combat ransomware is to prevent it from ever gaining a foothold in the first place. This involves a combination of technical safeguards and user education.
Robust Backup and Recovery Solutions
The cornerstone of ransomware defense is a comprehensive backup and recovery strategy. Regularly backing up critical data to an offline, isolated location (such as a separate external drive or a secure cloud backup service) ensures that even if files are encrypted, they can be restored without paying the ransom. It’s vital to test these backups regularly to confirm their integrity and the ability to restore data effectively.
Strong Cybersecurity Practices
Implementing strong cybersecurity practices is paramount. This includes:
- Regular Software Updates: Keeping operating systems, applications, and security software up-to-date with the latest patches closes known vulnerabilities that ransomware can exploit.
- Email Filtering and Antivirus Software: Utilizing advanced email filtering solutions to detect and block malicious attachments and links, along with reputable antivirus and anti-malware software that is kept current, provides a crucial layer of defense.
- Network Segmentation: Dividing a network into smaller, isolated segments can limit the lateral movement of ransomware if one segment is compromised.
- Least Privilege Principle: Granting users and applications only the necessary permissions to perform their tasks reduces the potential damage a compromised account or program can inflict.
User Education and Awareness Training
Human error remains a significant vulnerability. Educating employees about the dangers of phishing emails, suspicious links, and unsolicited attachments is vital. Regular training sessions on recognizing and reporting potential threats can significantly reduce the success rate of social engineering attacks.
Detection and Response
Even with the best prevention strategies, it’s essential to have mechanisms in place to detect and respond to a ransomware attack should it occur.
Endpoint Detection and Response (EDR) Solutions
EDR solutions monitor endpoint devices (computers, servers) for suspicious activity, providing real-time threat detection and enabling rapid incident response. They can identify the early signs of ransomware infection, such as unusual file access patterns or encryption activity, allowing security teams to isolate the affected systems before the ransomware can spread further.
Incident Response Planning
Having a well-defined incident response plan is crucial. This plan should outline the steps to be taken in the event of a ransomware attack, including:
- Containment: Isolating infected systems to prevent further spread.
- Investigation: Determining the scope of the attack and the type of ransomware involved.
- Eradication: Removing the malware from the infected systems.
- Recovery: Restoring data from backups and rebuilding compromised systems.
- Post-Incident Analysis: Learning from the attack to improve future defenses.
The Ethical Dilemma: To Pay or Not to Pay?
The decision of whether to pay a ransomware demand is a complex ethical and strategic one, with significant implications.
The Risks of Paying
Paying the ransom does not guarantee the recovery of data. Attackers may not provide a working decryption key, or the key may only partially restore the data. Furthermore, paying incentivizes further criminal activity and can label the victim as a willing target for future attacks. Law enforcement agencies generally advise against paying ransoms.

The Argument for Not Paying
The prevailing recommendation from cybersecurity experts and law enforcement is to avoid paying ransoms. This stance is based on the belief that paying fuels the ransomware economy and encourages more attacks. Instead, organizations are urged to focus on robust backup and recovery strategies, ensuring they can restore their operations without succumbing to extortion. The goal is to make paying a ransomware demand a futile and unprofitable endeavor for cybercriminals.
