In the modern era of unmanned aerial vehicles (UAVs), a drone is far more than just a collection of motors, propellers, and carbon fiber. It is a sophisticated, connected IoT (Internet of Things) device that relies heavily on a digital ecosystem. At the heart of this ecosystem is the drone application—a critical accessory that manages everything from flight telemetry to firmware updates and cloud-based storage of your cinematic captures. Most pilots link these apps to their primary email addresses to sync flight logs and manage insurance or registration details. However, this connectivity introduces a significant vulnerability.

If the email account associated with your drone accessories and software is compromised, the security of your entire flight operation is at risk. A hacked email isn’t just a personal inconvenience; it is a gateway for unauthorized individuals to access your flight history, sensitive GPS data, and even take control of your manufacturer-linked accounts. Here is a comprehensive guide on what to do when your drone-related email is hacked, and how to safeguard your hardware and data from digital intrusion.
Immediate Response: Severing the Link Between the Drone Ecosystem and the Compromised Account
The moment you realize your email has been compromised, your first priority is “damage control” within your drone’s software ecosystem. Because drone apps like DJI Fly, Autel Explorer, or Parrot FreeFlight are often set to “auto-login,” a hacker who gains control of your email can potentially trigger password resets and lock you out of your own flight management systems.
Disconnect the Smart Controller and Mobile Apps
Your first physical step should be to turn on your controller (especially if it’s a Smart Controller with an integrated screen) and manually log out of the flight application. If the hacker has already changed your password via the compromised email, the app may eventually de-authenticate you, but forcing a logout—if still possible—can prevent the sync of new flight data. If you use a tablet or smartphone as a controller accessory, ensure that the “Remember Me” credentials are cleared from the app’s cache.
Initiate an Emergency Password Reset via a Secure Device
Do not attempt to fix the problem using the same computer that may have been the source of the initial breach. Using a secure, secondary device, attempt to change your drone manufacturer’s account password immediately. If the hacker has not yet changed the recovery settings within the drone app, you may be able to migrate your account to a new, secure email address. This effectively “orphans” the hacked email, ensuring that even if the attacker maintains control of your inbox, they can no longer influence your drone’s cloud data.
Contact Manufacturer Support with Hardware Proof
If you are locked out of your drone account because the hacker was faster than you, you must contact the manufacturer’s technical support team (e.g., DJI, Skydio, or Autel). Most high-end drone systems are tied to a unique Serial Number (SN) found on the aircraft’s frame or inside the battery compartment. By providing proof of purchase and the hardware SN, you can verify your identity as the rightful owner, allowing the manufacturer to manually decouple the drone from the hacked email and re-assign it to a secure one.
The Risks of a Compromised Drone Ecosystem: Privacy, Flight Logs, and Financials
Understanding what is at stake is crucial for any pilot. When we talk about “drone accessories,” we are often referring to the software and cloud-syncing capabilities that make modern flight possible. A hacked email provides a roadmap to your entire aerial history.
Protecting Sensitive GPS Data and Home Points
One of the most significant risks involves your flight logs. These logs contain precise GPS coordinates of every takeoff and landing. For many hobbyists, the “Home Point” is their front yard or place of business. If an attacker gains access to your drone account through your email, they can download these logs and determine exactly where you live and where you store your expensive equipment. Protecting your email is, therefore, a matter of physical security as much as digital security.
Securing Cloud-Synced Footage and Media
Many modern drone apps offer a feature where low-resolution proxy files or even high-resolution images are automatically synced to a cloud gallery for quick sharing. If your email is hacked, your private imagery—which might include shots of private property, sensitive infrastructure, or personal moments—becomes accessible to the intruder. This is particularly dangerous for commercial pilots who may be under Non-Disclosure Agreements (NDAs) with clients regarding the data they collect.
Preventing Unauthorized Access to Remote ID and Registration
With the implementation of Remote ID and mandatory registration (such as the FAA’s DroneZone in the United States), your drone’s digital identity is strictly regulated. A hacked email could allow an attacker to alter your registration details or even report a drone as stolen/lost, creating a legal nightmare for the actual owner. Furthermore, if you have credit card information saved in the drone’s “In-App Store” for purchasing Care Refresh plans or additional software features (like specialized mapping plugins), those financial assets are immediately endangered.
Restoring Access and Validating Airworthiness
Once the immediate threat has been neutralized, you must focus on the long-term restoration of your drone system. A hacked account can lead to “corrupted” settings that might affect the flight performance or legal status of your UAV.
Auditing Flight Logs and Account Settings
Once you regain access to your drone account, perform a thorough audit. Look for any flight logs that you do not recognize. Hackers sometimes use compromised accounts to “mask” their own illegal flights, essentially spoofing their identity using your credentials. If you see flight activity in locations you have never visited, document it immediately and report it to the manufacturer to ensure you are not held liable for any airspace violations committed under your name.
Updating Firmware and Re-binding Accessories
A sophisticated breach might involve the hacker attempting to “bind” your drone to a different controller or remote. In the drone world, “Binding” is the process of linking a specific aircraft to a specific remote controller accessory. Check your app settings to ensure that your drone is only bound to your authorized hardware. It is also a best practice to perform a fresh firmware update on both the aircraft and the controller. This ensures that any malicious cached data is overwritten by a clean, factory-verified version of the operating system.
Re-registering with Aviation Authorities
If the compromised email was also the primary contact for your pilot’s license or drone registration, you must log into the government portal (like the FAA DroneZone or EASA equivalent) and update your security credentials. Ensure that your “Small UAS Certificate of Registration” is still valid and hasn’t been tampered with. This is an essential step in maintaining your legal status as an operator.
Preventative Security: Hardening Your Drone Hardware and Software
To prevent a recurrence of this situation, you must treat your drone’s digital accessories with the same level of care as your physical propellers and batteries.
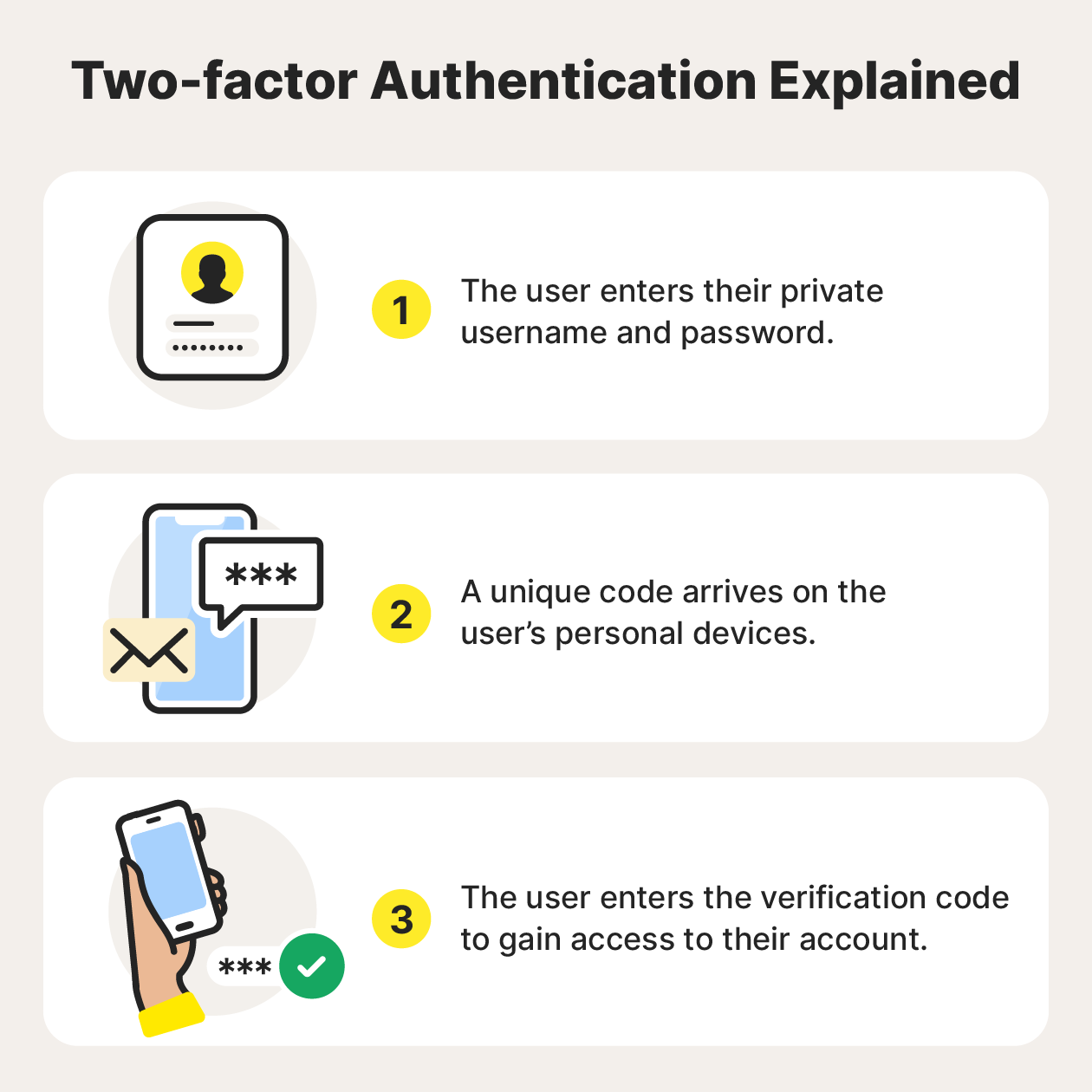
Implementing Two-Factor Authentication (2FA) for Drone Apps
Most major drone manufacturers now offer Two-Factor Authentication (2FA). This is the single most effective defense against email-related hacks. Even if an attacker gains access to your email, they will be unable to log into your drone account or change flight settings without a secondary code sent to your physical mobile device. Enable this feature immediately within your DJI, Autel, or Skydio profile settings.
Using Dedicated Emails for Flight Operations
A “pro tip” for serious aerial cinematographers and commercial pilots is to use a dedicated email address specifically for drone operations. Do not use the same email for your drone account that you use for social media or general web browsing. By creating a “siloed” email account that is only used for drone registration and app logins, you drastically reduce the surface area for a potential phishing attack.

Securing the Smart Controller and Mobile Interface
If you use a Smart Controller or a dedicated tablet as a flight accessory, ensure it has a screen lock (PIN or Biometric). Many pilots leave their controllers “open” for convenience, but if the hardware is stolen or accessed by an unauthorized person, they could potentially exploit the logged-in email and drone apps to cause significant damage. Furthermore, avoid connecting your drone’s controller to public Wi-Fi networks when downloading maps or updating firmware. Use a secure mobile hotspot to ensure the data transfer between the drone manufacturer’s servers and your accessory remains encrypted and private.
In conclusion, the modern drone is an extension of our digital lives. When your email is hacked, the ripple effects can ground your fleet and expose your private data. By acting quickly to sever the link, auditing your flight logs, and implementing robust 2FA protocols, you can ensure that your aerial adventures remain secure, private, and professionally managed. Your drone is a high-tech tool; treat the software and the email that powers it with the same precision you use when navigating through a narrow forest canopy or capturing a sunset at 400 feet.
