In an increasingly interconnected world, where data flows seamlessly across continents and devices communicate autonomously, the underlying mechanisms that orchestrate this complex ballet often remain invisible. At the heart of this digital symphony lies the concept of the computer network protocol – a set of rules that defines how data is formatted, transmitted, received, and interpreted across networks. Far from being a mere technicality, protocols are the foundational language that enables every interaction, from browsing a webpage to operating an autonomous vehicle, making them utterly indispensable to the fabric of modern Tech & Innovation. Without standardized protocols, the digital realm would descend into an unintelligible babel, with devices unable to understand each other, rendering the vast potential of technologies like AI, remote sensing, and the Internet of Things (IoT) utterly unattainable.
The Foundational Language of Digital Communication
To truly appreciate the significance of network protocols, one must first grasp their fundamental role as the universal grammar and lexicon of the digital world. They are the agreed-upon standards that dictate every aspect of digital communication.
Defining Network Protocols
A computer network protocol is, in essence, a formal set of rules and procedures for regulating data transmission between two or more devices. These rules specify how devices should initiate, maintain, and terminate communication sessions. They dictate everything from the physical medium of data transmission (e.g., electrical signals, radio waves) to the logical structure of data packets, error checking methods, and the algorithms for routing information through complex networks. Protocols ensure interoperability, meaning that devices from different manufacturers, running different operating systems, can reliably exchange information as long as they adhere to the same protocol standards. This standardization is what allows the global internet to function as a single, coherent entity.
Why Protocols are Indispensable
The necessity of protocols becomes apparent when considering the sheer diversity of hardware and software involved in even a simple internet transaction. A smartphone, a Wi-Fi router, an internet service provider’s server, and a website’s hosting server – all manufactured by different companies, potentially running different software – must all work together harmoniously. Protocols provide the common ground. They ensure that when your phone sends a request to a server, the server understands that request, processes it, and sends back a response that your phone can then interpret and display. Without this common understanding, communication would be impossible, leading to fragmented systems incapable of true integration or scalability. This foundational layer of agreement is what has allowed for the explosion of innovation in areas like cloud computing, big data analytics, and distributed ledger technologies.
Analogy: Human Language vs. Network Protocols
Consider how humans communicate. If two people want to converse, they must agree on a common language – say, English. Within English, there are specific rules (grammar, syntax) and a shared vocabulary. One person might ask a question (“What time is it?”), and the other understands the query and responds appropriately (“It’s three o’clock.”). Now, imagine one person speaking English and the other speaking Mandarin, with no shared understanding. Communication breaks down entirely. Network protocols serve precisely this role. They are the agreed-upon “languages” that allow computers and network devices to “speak” to each other, ensuring that messages are correctly formatted, transmitted, received, and understood, regardless of the underlying hardware or software specifics. This shared language is critical for advanced tech innovations that rely on complex, multi-party interactions.
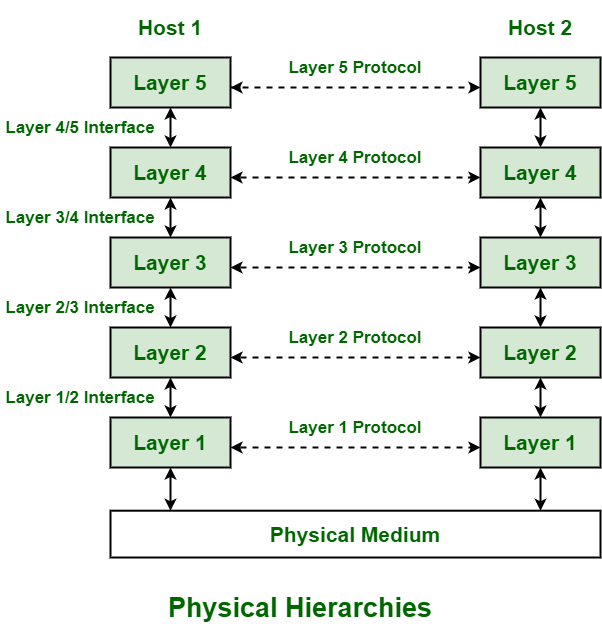
Architecture and Layers: The OSI and TCP/IP Models
To manage the immense complexity of network communication, protocols are not a single monolithic entity but rather organized into layered architectures. These layered models provide a structured way to think about and implement network functions, allowing for modular development and troubleshooting. The two most prominent models are the Open Systems Interconnection (OSI) model and the Transmission Control Protocol/Internet Protocol (TCP/IP) model.
The OSI Model: A Conceptual Framework
Developed by the International Organization for Standardization (ISO) in the 1980s, the OSI model is a seven-layer conceptual framework that standardizes how different communication systems should communicate with each other. Each layer provides services to the layer above it and receives services from the layer below. The layers are:
- Physical Layer: Deals with the physical transmission medium (cables, Wi-Fi signals).
- Data Link Layer: Handles frame synchronization, error control, and physical addressing (MAC addresses).
- Network Layer: Manages logical addressing (IP addresses) and routing of data packets.
- Transport Layer: Ensures reliable, end-to-end delivery of data, managing segmentation and reassembly.
- Session Layer: Establishes, manages, and terminates communication sessions.
- Presentation Layer: Translates data into a format the application layer can understand (e.g., encryption, compression).
- Application Layer: Provides network services directly to end-user applications (e.g., web browsers, email clients).
While largely a theoretical model, the OSI framework is invaluable for understanding how networks function and for troubleshooting network issues, offering a clear demarcation of responsibilities.
The TCP/IP Model: The Internet’s Backbone
The TCP/IP model is a more practical, four-layer model that underpins the entire internet. It predates the OSI model and combines some of the OSI layers for efficiency. Its layers are:
- Network Access Layer (OSI Physical + Data Link): Deals with hardware addressing and physical transmission.
- Internet Layer (OSI Network): Handles logical addressing (IP) and routing.
- Transport Layer (OSI Transport): Manages end-to-end communication, often using TCP for reliable connections or UDP for faster, less reliable ones.
- Application Layer (OSI Session + Presentation + Application): Contains protocols that interact directly with applications (e.g., HTTP, FTP, SMTP).
The TCP/IP model’s pragmatic design has made it the de facto standard for internet communication, proving its robustness and scalability over decades of technological evolution.
How Layers Facilitate Innovation
The layered approach is crucial for innovation because it allows developers to focus on specific functionalities without needing to understand the intricacies of every other layer. For example, an application developer building a new AI-powered service can rely on the transport layer (TCP) to ensure their data gets from point A to point B reliably, without needing to know how the network layer routes packets or how the physical layer transmits bits. This abstraction fosters modularity, accelerates development cycles, and allows for specialized innovations at each layer, from new physical transmission technologies (like fiber optics) to advanced application-level protocols for distributed computing or quantum communication.
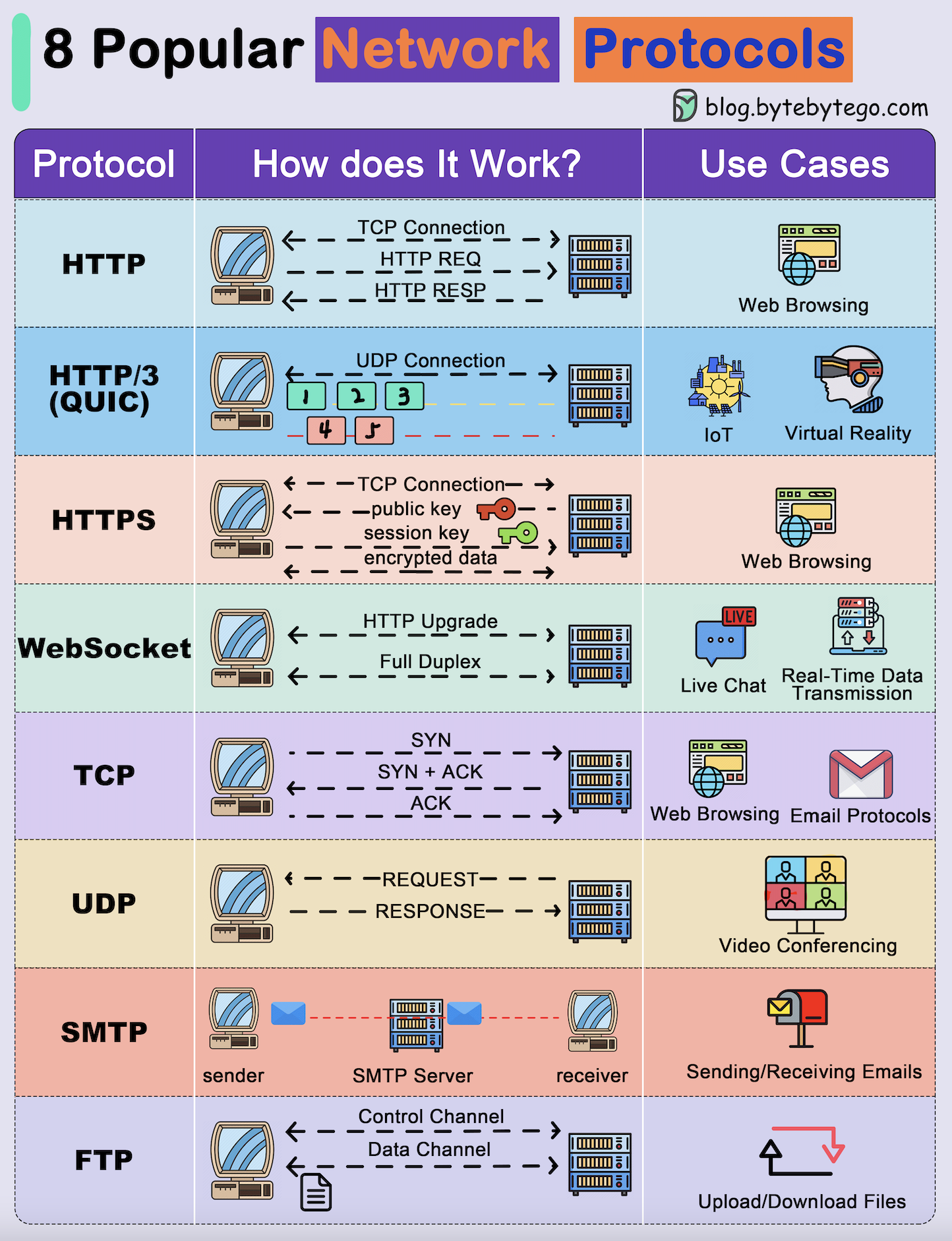
Key Types of Network Protocols and Their Functions
Within these layered architectures, numerous specific protocols perform distinct functions, each contributing to the overall coherence and efficiency of network operations.
Application Layer Protocols (HTTP, FTP, SMTP, DNS)
These protocols are closest to the end-user, facilitating specific services that applications provide:
- HTTP (Hypertext Transfer Protocol): The foundation of data communication for the World Wide Web, allowing web browsers to request and receive web pages.
- FTP (File Transfer Protocol): Used for transferring files between a client and a server on a computer network.
- SMTP (Simple Mail Transfer Protocol): The standard for sending email across IP networks.
- DNS (Domain Name System): Translates human-readable domain names (e.g., google.com) into machine-readable IP addresses, a critical service for internet navigation. These protocols enable the vast array of web-based applications, cloud services, and real-time data streaming that characterize modern innovation.
Transport Layer Protocols (TCP, UDP)
These protocols manage end-to-end communication between applications:
- TCP (Transmission Control Protocol): A connection-oriented protocol that provides reliable, ordered, and error-checked delivery of a stream of bytes between applications. It’s used for applications where data integrity is paramount, like web browsing, email, and file transfers.
- UDP (User Datagram Protocol): A connectionless protocol that offers a faster but less reliable service. It’s suitable for applications where speed is more critical than guaranteed delivery, such as online gaming, voice over IP (VoIP), and live video streaming, especially where slight data loss is tolerable. The choice between TCP and UDP profoundly impacts the performance and reliability of innovative applications.
Network Layer Protocols (IP, ICMP)
These protocols handle the logical addressing and routing of data packets across networks:
- IP (Internet Protocol): The primary protocol for delivering data packets across network boundaries. It defines the addressing scheme (IP addresses) and how packets are routed from a source host to a destination host, often across multiple intermediate networks. Both IPv4 and the newer IPv6 are crucial for connecting the ever-growing number of devices in the IoT and other advanced systems.
- ICMP (Internet Control Message Protocol): Used by network devices, like routers, to send error messages and operational information, such as whether a requested service is unavailable or if a host or router could not be reached. It’s vital for network diagnostics.
Data Link and Physical Layer Protocols (Ethernet, Wi-Fi)
These protocols manage communication within a local network segment and the actual transmission of bits:
- Ethernet: The most widely used wired LAN technology, defining how data is formatted and transmitted over an Ethernet cable.
- Wi-Fi (IEEE 802.11): A family of wireless networking protocols that allow devices to connect to a network wirelessly.
These lower-layer protocols are the bedrock upon which all higher-level communications depend, enabling the physical connectivity that powers everything from smart homes to massive data centers.
Protocols in the Era of Tech & Innovation
The foundational role of network protocols is especially pronounced in the context of cutting-edge technologies that drive our future.
Enabling Autonomous Systems and AI
Autonomous vehicles, drones, and robotic systems rely heavily on continuous, low-latency, and reliable communication. Protocols ensure that sensor data (Lidar, radar, cameras) is efficiently transmitted to onboard AI processing units, and that control commands are relayed back to actuators without delay. In distributed AI systems, where machine learning models are trained across multiple servers or edge devices, robust protocols are essential for synchronizing data, sharing model updates, and orchestrating complex computations across a network. Furthermore, the emergent field of swarm robotics, where multiple robots cooperate to achieve a common goal, is entirely dependent on sophisticated, real-time communication protocols that enable inter-robot coordination and decision-making.
Powering Remote Sensing and IoT
Remote sensing, whether from satellite imagery or drone-mounted sensors, generates enormous volumes of data that must be transmitted, stored, and analyzed. Network protocols facilitate the efficient transfer of this imagery and sensor data from collection points to data centers for processing, often over vast distances and with varying bandwidth availability. The Internet of Things (IoT), with its billions of interconnected devices ranging from smart thermostats to industrial sensors, also relies heavily on specialized protocols. Low-power wireless protocols like Zigbee, Z-Wave, and LoRaWAN enable devices to communicate efficiently over long ranges with minimal power consumption, while lightweight application protocols like MQTT (Message Queuing Telemetry Transport) are optimized for constrained IoT devices to send small messages reliably, even in unreliable network conditions. These protocols are the invisible backbone enabling the smart cities and connected environments of tomorrow.
Securing Future Innovations with Protocol Enhancements
As technology advances, so do the threats to network security. Protocols are continually evolving to incorporate robust security measures. Secure versions of common protocols, such as HTTPS (HTTP Secure, using TLS/SSL encryption), SFTP (Secure FTP), and secure VPN protocols, are crucial for protecting sensitive data from cyber threats. For future innovations like quantum computing and quantum communication, new protocols are being developed to leverage quantum phenomena for inherently secure data transmission. Furthermore, blockchain technology, which underpins cryptocurrencies and decentralized applications, is itself a novel protocol stack designed to ensure data integrity and security through cryptographic means in a distributed network.
The Evolving Landscape of Network Protocols
The world of network protocols is dynamic, constantly adapting to new demands and technological advancements.
Challenges: Latency, Bandwidth, and Security
The continuous push for higher bandwidth, lower latency, and enhanced security presents ongoing challenges for protocol designers. The advent of real-time applications like virtual reality, augmented reality, and critical communication in autonomous systems demands protocols that can guarantee extremely low latency and high reliability. Simultaneously, the proliferation of data-intensive applications and the sheer volume of IoT devices necessitate protocols that can efficiently manage massive amounts of data traffic without congestion. The increasing sophistication of cyber threats also means that protocols must continually be updated and fortified to withstand new forms of attack, ensuring the integrity and privacy of information.
Future Trends: 5G, Quantum Networking, and Beyond
The evolution of network protocols is intrinsically linked to emerging technologies. The deployment of 5G networks, for instance, introduces new capabilities like network slicing and ultra-reliable low-latency communication (URLLC), which require new protocol extensions and optimizations at various layers to fully realize their potential for applications like remote surgery or industrial automation. Beyond 5G, research into quantum networking promises to revolutionize secure communication by leveraging the principles of quantum mechanics, demanding entirely new classes of quantum protocols. Furthermore, the growing adoption of decentralized systems and edge computing will necessitate more efficient peer-to-peer protocols and mechanisms for distributed consensus, pushing the boundaries of what network protocols can achieve in terms of resilience, scalability, and efficiency.
In conclusion, computer network protocols are not merely technical jargon but the foundational bedrock upon which all modern Tech & Innovation is built. They are the silent enablers of global connectivity, allowing disparate systems to communicate, collaborate, and create new possibilities. From the simple act of browsing a website to the complex orchestration of autonomous fleets, protocols ensure that the digital world functions cohesively. As we venture further into an era defined by AI, IoT, autonomous systems, and ever-increasing interconnectedness, the continuous evolution and robust implementation of these essential rules will remain paramount to unlocking the full potential of human ingenuity and technological advancement.

